basic and effective security with pi-hole
Ad blockers are useful (yes), but this solution is relatively complex to deploy on each software, doesn’t cover all threats since targeting mainly advertisement and does not cover simple embedded devices like IOT for example.

At home or in small companies, it is not easy to have advanced security devices and configure DNS server of installing specific solution is not easy for everyone. But there is a simple solution that could enable a first security level based on DNS filtering. Effectively, all URL accessed by devices on the network will require a name to IP address resolution, this is performed by a DNS server and filtering at this level allows a first level of security by implementing white and black lists. The pi-hole solution is really simple to install and allows a first level of filtering which is really efficient.
You are probably using at home or in your office multiple devices, some smart phones, a vocal assistant, maybe a connected fridge, a game console, a printer, a weather station, a connected TV screen and probably you don’t exactly know how much communication these devices are doing on the internet. If you ask yourself if any valuable information about yourself, your family or your company are also going out of your network I can confirm that you will be surprised. Maybe on your favorite computer you have installed a browser ad-blocking extension, but on all the other devices, did you do something? In the future, more and more connected devices will be used in our environment, it will be impossible to control easily their exchanges knowing that most people are not using a network traffic analyzer.
The solution: pi-hole
Pi-hole solution is presented as a black hole for internet advertisements. Even if the main usage of this solution is effectively to block ads, it is also a very good solution to block other threats like malware, crypto currencies mining scripts, ransomware command and control or binary distribution sites, telemetry and other collecting solution mainly used by internet giant providers to collect our activities, habits or simply localization and presence.
How does it work
The base principle of pi-hole is to serve all the devices on the local network as a DNS server and based on black and white lists provide either the real IP address or the one of the pi-hole itself. The local server will explain that this resource is filtered. Most of the time the DNS request in the blacklist would have allowed the browser to gather a javascript file or pushing an information through a POST method, thus you will not notice anything on a standard browser.
One of the main advantage of this method based on the DNS resolution is that it works independently of the protocol, even TLS request (ie in https) will be filtered out without requiring an inspection of the request or the TLS session. This URL filtering function is generally performed for ciphered transaction on specific firewall modules which are expensive most of the time.
In order to be effective, it is mandatory for pi-hole to replace your DNS server which is probably provided by your ISP. The configuration of the DNS server is most of the time pushed within DHCP negotiation by the customer edge installed at your home or office by your internet provider, a specific configuration will then be required. Either you will have to change the DNS information in the DHCP section of the CE or disable the DHCP and let pi-hole handle this function. I do recommend this option if possible, since it enables pi-hole to present the name of the devices on the local network based on their IP address.
Installation
As we can suspect from the name of the solution, the normal installation will require a Raspberry PI device. This technical approach is interesting since the device will have to be powered up 24x7 but does not require a lot of computing nor storage to perform well. It is easy to find, not expensive, noiseless and easy to install in a closet, near the printer or the TV set. Even if you think yourself able to install the whole solution on the linux server, it is a waste of time. The PI is really efficient in this situation.
I started the first installation on a PI 1 B+ series, not powerful but enough for this job at home. For sure, you can use any model of the PI available, the latest model is around 40€ with the power supply if you don’t have one available.
You will find on the web site the whole installation process, very easy if you have already played with a raspberry, otherwise you will need some more documentation from the raspberry web site (ie enable ssh for remote access). Some small adjustments will be required if you want a perfect installation, like the time synchronization or the web server answering also on the https port, but these are optional to start with.
Advanced configuration
The web interface of the pi-hole allows access to statistics, log files, list configuration (black and white) and to configure some parameters of the system (dns sources, dhcp options and ranges, ip address). Some few administration actions can be performed from this interface like restart, disable the system for test purpose or refresh the list.
Block lists
By chance, white and black lists can be extracted from specific sources on the internet, some are already proposed with the default installation, but some others can be added. Even if a specific domain is in multiple lists, pi-hole will keep only one instance of each. By design of the technical solution, be certain not to add an url list, there are a lot of these on internet but more designed for firewall and proxy filtering, here we could only add domain names.
For the additional list you could add, you could start with:
- crypto currency mining: CoinBlockerLists
- ransomware: ransomwaretracker, pick RW_DOMBL list at least
- scams: Spam404
DNS
Since pi-hole is acting as a DNS proxy (through the dnsmasq module of linux), you could configure the servers you will rely on. Adding multiple sources will disable the tracking some servers are able to perform on multiple request from the same source. Think about mixing IPv4 and IPv6 resolvers since more and more traffic is flowing over IPv6. In the proposed list with the default installation, you will find Google, OpenDNS, Level3, Norton, Comodo, DNS.WATCH and Quad9, you can add some more if you want, the one of your ISP for example.
API/Web interface
The web interface is rich and easy to use, you can configure it in order to hide some domains from the statistics. This will allow you to have information on domains less used but that could hide some traffic from specific devices to the vendor site, but for this purpose you need to suppress the first one (facebook, google, …).
Teleporter
The last menu of the configuration part of the site allows to download in an archive the whole configuration in order to push it on another device or simply perform a backup. Nice feature.
First Results
In order to push you to install this solution on your network, here are some of the first results I gathered on my installation at home, basic network with some various equipment (PC, phones, TV, connected music player, …)
Global status
The interface proposed without authentication is simple and presents some basic stats, easy to check the traffic, the blacklist volume and global performance of the filtering.
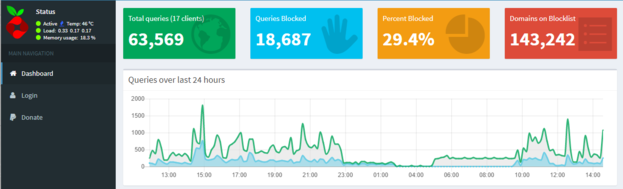
Here, you can see that the system load is around 0.35 over the last 5 minutes, PI 1 version is enough for this kind of usage. The blacklist size is around 140k entries and the filtering performance at 29%, meaning that 29% of the DNS requests will be filtered out.
DNS Statistics
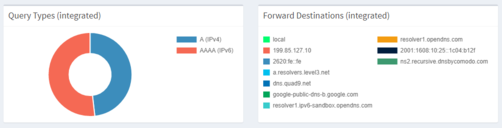
On the left graph, you will see the IPv4 versus v6 used on my network, on the right-hand side all the servers used for the recursion of the DNS request.
Audit log
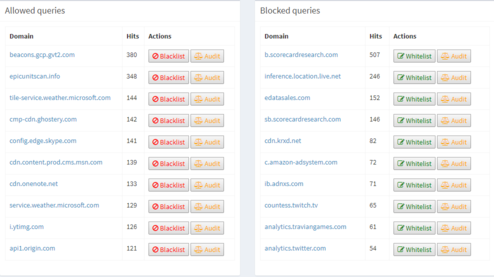
The audit view will allow to see the used domains (left) and the filtered one (right). These views allow to manually add entries in the white and black lists, also to hide the domain from the statistics views. These lists will be really useful at the beginning of the installation since you will see all the fancy domains contacted by the devices on your network and you could filter in or out based on whether you think it is useful or not.
API
If you want more advanced usage of your pi-hole solution, you can integrate statistics in your reporting or application through the API which is available, for example:
1http://pi-hole.local/admin/api.php?summary
2{
3 "domains_being_blocked": "143,242",
4 "dns_queries_today": "61,477",
5 "ads_blocked_today": "18,116",
6 "queries_forwarded": "27,207",
7 "queries_cached": "16,154",
8 "clients_ever_seen":"17",
9 "unique_clients":"16",
10 "ads_percentage_today": "29.5",
11 "unique_domains": "2,138",
12 "status":"enabled"
13}
Conclusion
With very little installation and roughly an hour of work you could enable a first level of filtering efficient on your network. This will simplify the browsing on any device by suppressing some ads and more important protect in some way your devices. More important, your actions on internet will be more complex to track by providers and this is a good solution for personal information and net privacy.
Photo from Bernard Hermant